Introduction to Quantum Cryptography
Quantum cryptography is a new method of cryptography that it’s based on quantum mechanics laws, pretending that uncertainty has the potency to weaken the ability of an intruder to hack or get into a system by boosting the entropy.
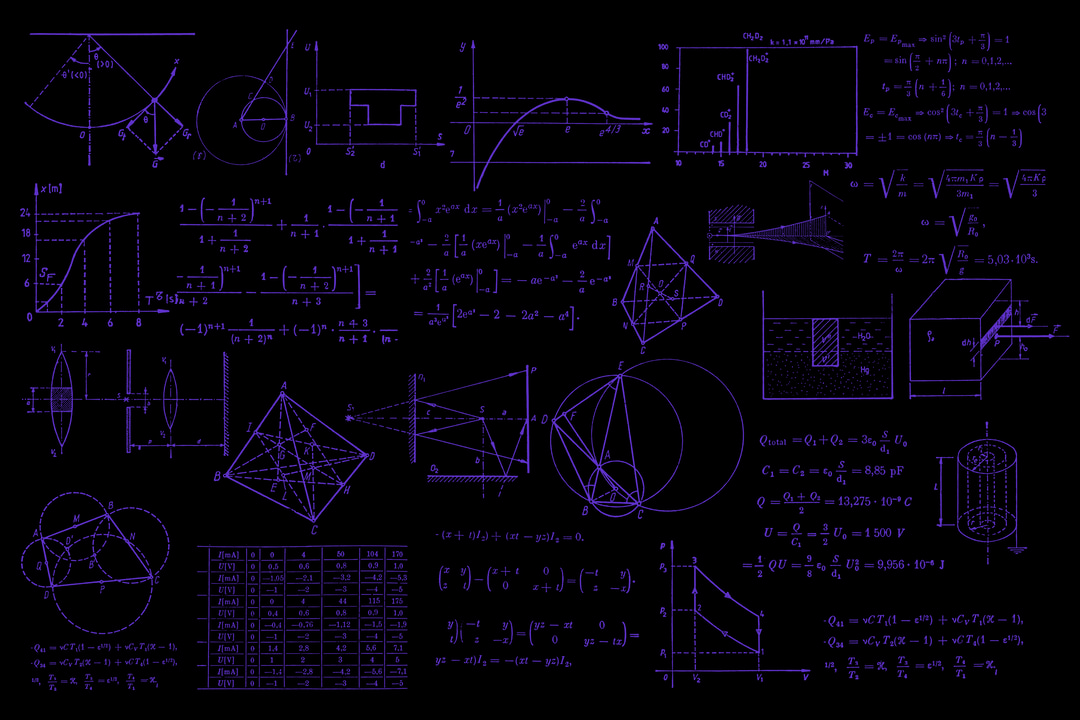
Relying on the Heisenberg uncertainty principle, we assume that one cannot detect accurately anything depending on this function:
A developed quantum cryptosystem (a cryptosystem that will use the roles of quantum mechanics) will maintain a secure system.
So now, what is quantum cryptography in terms of quantum mechanics? It states that using the photons and their axiom quantum characteristics to establish a non-breakable cryptosystem due to the condition that a quantum condition or state cannot be computed or measured without warning the system.
Photons are the core of quantum mechanics, and by using them you guarantee that you’re using the smallest known particles in the universe.
And as per Schrodinger, a quantum system will remain as it’s until it reacts or is manipulated with an external medium “considering the cat, the cat is dead and alive at the same time until observation”.
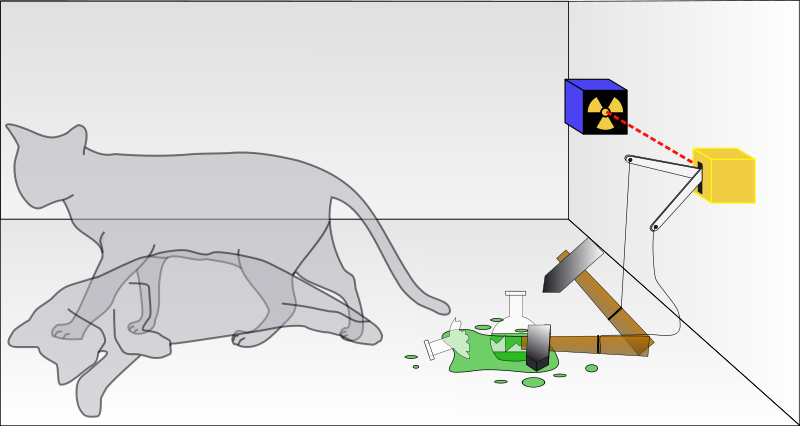
We can assume that Newton's first law “an object will remain to conduct its motions or in rest until it gets affected by an external action or force" so will have the same theory as Schrodinger's cat theory.
Photons can be in different states at the same time, and as it gets measured they will change their state concurrently. And this statement above was believed as the core of quantum cryptography.
Upon exchanging a message between the sender and the receiver, it travels through a channel, which when intercepted by any malicious entity, exposes the change in the state of the photon, therefore making it visible to the sender/receiver.
On the other hand, Quantum Entanglement can be used, when a system subsists of two photons, any change affecting the first one, leads to a change in the other, thereby making intruders’ actions in networks detectable.
Quantum Key Distribution
QKD, is one of the quantum cryptography elements, considering that Quantum Computers are exploiting photons to broadcast data.
As we mentioned earlier, a photon is a smallest known particle, it has a lineament designated as a spin, which has four sorts; 45 ° and - 45 ° Diagonal, horizontal, and Vertical, which is in QC illustrated as, binary 1 for horizontal & 45° diagonal, and 0 for vertical & -45° diagonal.
Uncertainty, A rubric states that adjusting the characteristics of a particle changes its state. Using that principle, an unknown connection becomes detectable by changing the state of a photon.

Device- Independent Cryptography
Another method of quantum encryption, it adjusts the genuine QKD so it is invulnerable and not touchable in a condition that unauthorized or obtrusive party devices are linked.
BB84
Bennett and Brassard proposed the BB84 which is the headmost quantum cryptography protocol in 1984.
Quantum cryptography isn’t used to convey message data, it is mainly used for the Implementation of, and this function is used with a specified encryption algorithm to (encrypt/decrypt) the message designated to be sent and transmitted through a classical communication channel.
In quantum cryptography methods, Alice and Bob can detect if any intruders or a third party are accessing the secured channel with them or trying to obtain the key, and this is by implementing the quantum super-positions and transmitting data in the quantum condition through a quantum channel.
BB84 was implemented in the physical layer as what was examined by Bennett and Brassard. It uses the conveyance of polarized photons which was discussed above in photon spins vectors. It needs to be located on two different bases.
Shor's Factoring Algorithm
This algorithm factorizes N (non-prime integer), finding integers p1 and p2 so it will produce, P1P2=N. The parts of this algorithm are:
- Preprocessing – preparing quantum registering by quantum parallelism and classical algorithms.
- QFT (quantum Fourier transform) – applied on the output of the preprocessing
- Post-processing and measurement using classical algorithms.
Difference between Classical Cryptography and Quantum cryptography
Classical cryptography is mainly based on mathematical algorithms and methods, it is durable by the point the private key is classified, and it is hard to use reverse engineering to calculate the private key.
Mathematically it is not possible to get the private key by reverse calculations and this can be one of the largest vulnerabilities. In contrast, QKD is the procedure of distribution of Secret keys, where security is properly established.
Quantum cryptography will accomplish having a secure environment, relies on itself, and also the information and communications are secured. It is accomplishing all the criteria by utilizing the laws of Quantum Mechanics with a view to executing a cryptographic It was proved by researchers that public-key cryptosystems can be compromised by quantum computers.
Mathematical proofs can’t be enough to ensure the security of quantum cryptography protocols. Quantum cryptosystems are not easy to be designed and implemented, due to the accuracy needed to avoid security flows.
Conclusion
it is fascinating how physics can be implemented in different aspects, quantum cryptography was a novel field in the conjunction between quantum mechanics (physics mainly) and Cryptography. It still needs more implementation on post-quantum systems and while creating new cryptographic methods, it is important to focus on developing the current methods that are being accessed by hackers and intruders.
we have gone through quantum computing earlier where we discussed the basics of quantum physics and the revolutionary idea of quantum computing, also in that article we discussed the hello world quantum program! quantum cryptography and quantum computing are very big subjects and it really needs more research to be done!
If you have a problem and no one else can help. Maybe you can hire the Kalvad-Team.